Our Stories
Who Should Support or Maintain the IT Infrastructure?
The backbone of any successful organization is its IT infrastructure. This intricate web of...
Understanding 3 Types of Backups: Full, Incremental, and Differential
In the contemporary realm of business operations, data is an essential asset, shaping and...
What is Network Security: A Complete Guide
In the intricate landscape of modern business, robust network security measures stand sentinel,...
10 Reasons Why Your Business Needs a Managed Services Provider
In the rapidly evolving technological landscape of modern business, staying ahead of the curve is...
Ten Things You Should Ask Your IT Provider Today
The cybersecurity landscape continues to rapidly evolve. Even before the COVID-19 pandemic hit,...
What To Look For in a Managed Services Provider: 9 Helpful Tips
In today’s rapidly evolving business landscape, organizations increasingly rely on technology to...
VoIP vs Landline: Which Phone System Is Better?
Clear, efficient, and convenient communication is key for organizations looking to streamline...
VoIP Customer Service: How It Works & Benefits
Customer service is an essential element of any business. Team members tasked with customer...
Technology Consulting: Strategies to Improve Your Business
Technology plays a critical role in a wide range of businesses and industries. When properly...
What is Technology Consulting? A Guide for Business Owners
For any business to be successful in this day and age, they need to harness the power of...
Understanding The Top 5 Authentication Methods In It Security
While passwords are critical for controlling access to sensitive areas, such as proprietary...
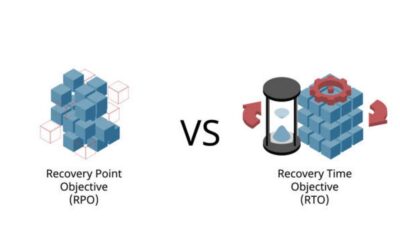
RTO vs RPO: Understanding Their Roles in Disaster Recovery Planning
Recovery Time Objective (RTO) and Recovery Point Objective (RPO) are two of the most essential...
Does Virtualization Impact CPU Performance?
Whether on computers, the internet, smartphones, iPads, or other PDA devices, virtualization is...
What is Disaster Recovery Testing? How Often Should It Be Done?
Even as digital technology advances at breakneck speed, disasters are still inevitable. Usually,...
How Often Should You Test Your Business Continuity Plan?
In order to stay competitive, relevant, and profitable, an organization can’t afford to be out of...
Is Information Security the Same as Cyber Security?
The terms information security and cyber security are sometimes used interchangeably, which can...
Understanding Cybersecurity Vulnerabilities And Their Types
When protecting your IT system, several robust cyber security countermeasures must be established...
Cyber Insurance Coverage: What is Covered & What is Not
As technology-enhanced commerce continues to grow at a rapid pace, organizations with digital...
How to Find the Best VoIP for Your Small Business
For a small business to be successful, clear and efficient communication is essential, which is...
What is EDR in Cyber Security & Why Is It Important?
When protecting an organization’s IT system and data, robust cybersecurity measures are a must....
Want to know what we can do for you?
Tyler: 903-581-7000
Longview: 903-757-5900

Contact
Tyler:
903-581-7000
Fax: 903-581-7629
Longview:
903-757-5900
Fax: 903-757-8657